Cryptocurrency cold storage refers to the practice of storing digital assets completely offline, disconnected from the internet and any network-accessible system. This method protects private keys from online threats such as hacking, phishing, and malware by storing them in a physical or air-gapped environment. Cold storage is considered one of the most secure methods for safeguarding long-term cryptocurrency holdings.
Unlike hot wallets, which are connected to the internet and used for frequent transactions, cold storage prioritizes security over convenience. Investors, custodians, and institutions often utilize cold storage to safeguard substantial sums of cryptocurrency, particularly when those assets are not required for day-to-day transactions.
Cold storage methods isolate private keys, preventing them from interacting with online systems. This reduces the attack surface and enhances the security of the stored assets.
The process typically begins with generating a key pair in an offline environment. This key pair includes the private key, which grants access to the cryptocurrency, and the public key, which others can use to send funds to the wallet. Offline key generation ensures that the private key never comes into contact with an internet-connected device. Tools used for this purpose often include secure computers running open-source wallet software or specialized hardware devices.
To send funds from cold storage, a transaction is created on an internet-connected device and then transferred (usually via QR code or USB) to an offline device for signing. Once signed, the transaction is moved back to the online system to broadcast it to the blockchain. This method keeps the private key isolated throughout the process, ensuring that even though the transaction must eventually be sent online, the sensitive key data remains in a protected environment.
An air-gapped device has no physical or wireless connection to the internet. This setup is commonly used in cold storage systems to prevent any form of remote access or compromise. These devices often run minimal software and are used solely for key management and transaction signing.
There are several cold storage options available, each with varying levels of security, accessibility, and user involvement.
A hardware wallet is a physical device specifically designed to store private keys securely. It connects to a computer or mobile device only when signing transactions and typically requires physical confirmation (e.g., pressing a button) to authorize actions. These devices are widely used for personal cold storage. They are compact, portable, and considered safer than hot wallets, but still depend on the user's ability to protect the device and its backup seed.
A paper wallet is a physical document that contains the public and private keys of a cryptocurrency wallet, often represented as alphanumeric strings or QR codes. It is generated offline and can be stored in a secure location such as a safe or vault. While inexpensive and fully offline, paper wallets require careful handling. If the paper is lost, damaged, or accessed by someone else, the associated funds may be irretrievable.
Some users engrave or imprint wallet recovery phrases (also known as seed phrases) onto metal plates. This method protects critical key recovery data from fire, water, and physical degradation that could affect paper or digital backups. Metal backups are often used in conjunction with other cold storage solutions. They don’t store keys or sign transactions themselves but serve as a long-term recovery method in case of device failure or loss.
An older or unused computer can be configured for cold storage by wiping its drive, disconnecting network interfaces, and installing Web3 wallet software offline. Similarly, private keys can be stored on encrypted USB drives kept in physically secure locations. These setups require technical knowledge and discipline but can provide a high level of security when properly implemented.
Cold storage plays an important role in safeguarding cryptocurrency, especially for individuals or organizations managing long-term holdings or large amounts.
By keeping private keys completely offline, cold storage removes exposure to the most common cyberattack vectors. There is no risk of keylogging, phishing, or malware accessing the private keys from an internet-connected device. This makes cold storage ideal for safeguarding against remote theft. Attackers would need physical access to the storage medium to attempt unauthorized access.
Cold storage is well-suited for investors with a long-term strategy. Since transactions are infrequent, the reduced accessibility does not hinder portfolio goals. Keys remain safe even during extended market inactivity. Many institutions also utilize cold storage to comply with internal policies or external regulations that require the use of secure custodial practices.
Users retain full custody of their assets and don’t rely on third-party platforms. With proper storage and backup, control remains entirely in the owner's hands. This aligns with the decentralized ethos of cryptocurrency. However, it also places full responsibility for security, backup, and loss prevention on the user.
Although highly secure, cold storage is not without its own risks. Proper implementation and backup management are crucial to prevent permanent data loss.
If a paper wallet is destroyed or a hardware wallet is lost without a recovery backup, the assets stored on it become inaccessible. There is no central authority responsible for recovering funds. Users must implement secure backup and recovery processes, including redundancy and safe storage in multiple physical locations when possible.
Cold storage is not designed for frequent access or real-time trading. Moving funds in and out requires deliberate steps, which may be too slow for users needing quick access to capital. This makes cold storage impractical for active traders or those relying on frequent payments or portfolio rebalancing.
Some cold storage solutions require technical knowledge to be implemented securely. Mistakes in key generation, storage, or backup procedures can compromise the safety of the assets. Without a clear understanding of wallet management and cryptographic principles, users risk exposing themselves to errors or vulnerabilities.
While cold storage is known for its enhanced security, hot storage remains widely used for convenience and daily transactions. The table below compares the key differences between the two methods.
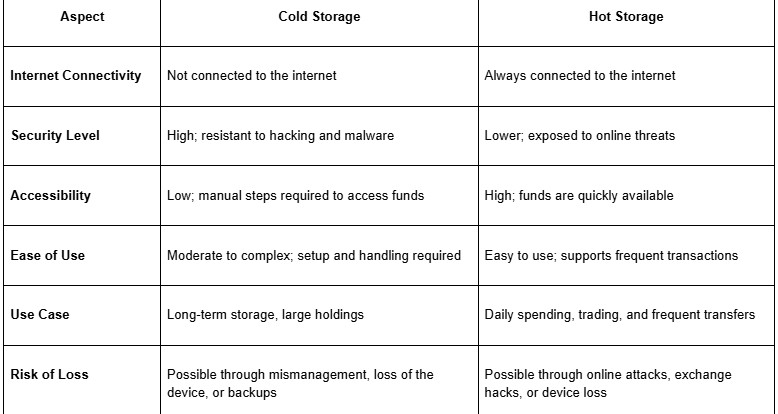
Cold storage serves different types of users who prioritize long-term security and control over convenience.
Individuals who invest in cryptocurrency with a multi-year time horizon benefit from cold storage. It removes funds from internet exposure and reduces the temptation to trade impulsively. These users typically perform transactions infrequently and focus on asset preservation.
Custodial firms, funds, and exchanges use cold storage to protect client assets. By keeping reserves offline, institutions reduce risk and improve compliance with security standards. Cold wallets often form part of a broader custody strategy that includes multi-signature approval, access auditing, and insurance coverage.
Cold storage can also play a role in digital asset inheritance. With proper documentation and backup procedures, it enables beneficiaries to access funds in the event of death or incapacity. This requires thoughtful planning and may involve lawyers or trusted third parties to ensure smooth access without compromising security.